CyberShield
Complete Website Protection with CyberShield WAF
CyberShield is a Next-Gen WAF designed to actively protect your Website & CMS from emerging threats and cyberattacks.
One WAF. Total Protection for all platforms and custom sites



Protect & Secure
Why You Need CyberShield for Web App Security
Web applications and websites are often the first layer targeted by cybercriminals because they represent a critical attack surface. These platforms are vulnerable to a wide range of attacks, making them prime targets for hackers.
As the entry point to your digital infrastructure, securing these applications is crucial to safeguard your data, maintain customer trust, and ensure the continuity of your operations.

- Cybershield is a Next-Gen Web Application Firewall designed to analyze security events in real time, detect attacks, quickly neutralize them, and notify administrators.
- Cybershield is a full-featured, cloud delivered web application security service, can be deployed in just minutes, ensuring complete protection for all your websites and apps.
- Cybershield protects websites and web applications from a wide range of web attacks and threats, including SQL injections, XSS vulnerabilities, and malicious bots.
- CyberShield enables users to display all logs and integrate modules for efficient security management. Additionally, Cybershield offers real-time monitoring to ensure continuous protection and rapid threat mitigation
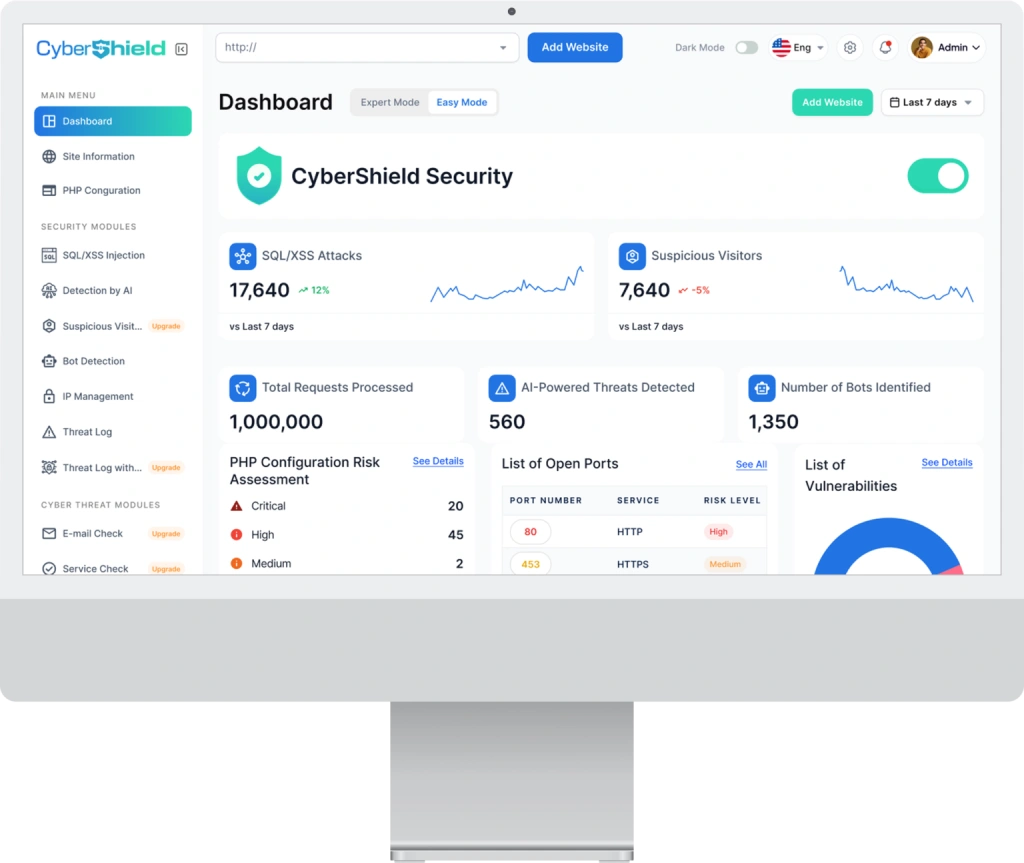
Our Product Overview

Our Solution In Numbers
Why Choose CyberShield?
Get Started in 5 Minutes
Simply install the plugin with a few clicks, quickly create your account, and start securing your web applications immediately.
Easy To Use
CyberShield WAF offers an intuitive user experience that requires no cybersecurity skills, enabling users of all backgrounds to effectively safeguard their web applications.
Real Time Control & Monitoring
CyberShield WAF provides real-time detection and blocking of attack attempts. The intuitive dashboard offers real-time insights into both attempted and blocked attacks, along with detailed information about malicious requests.
Instant Alerts: Stay Informed, Stay Ahead
CyberShield WAF keeps you in control with instant email alerts. Our system redirects attackers and prevents them from reaching your web application or website
1 Solution - Multi-Site Security
With CyberShield WAF, you're not limited to securing a single site. You can add as many sites as you need to manage multiple businesses - all under one account.
Cost-Effective
Our pricing plans are designed to fit the budgets of businesses of all sizes, from startups to enterprises.
Modules
CyberShield Modules
-
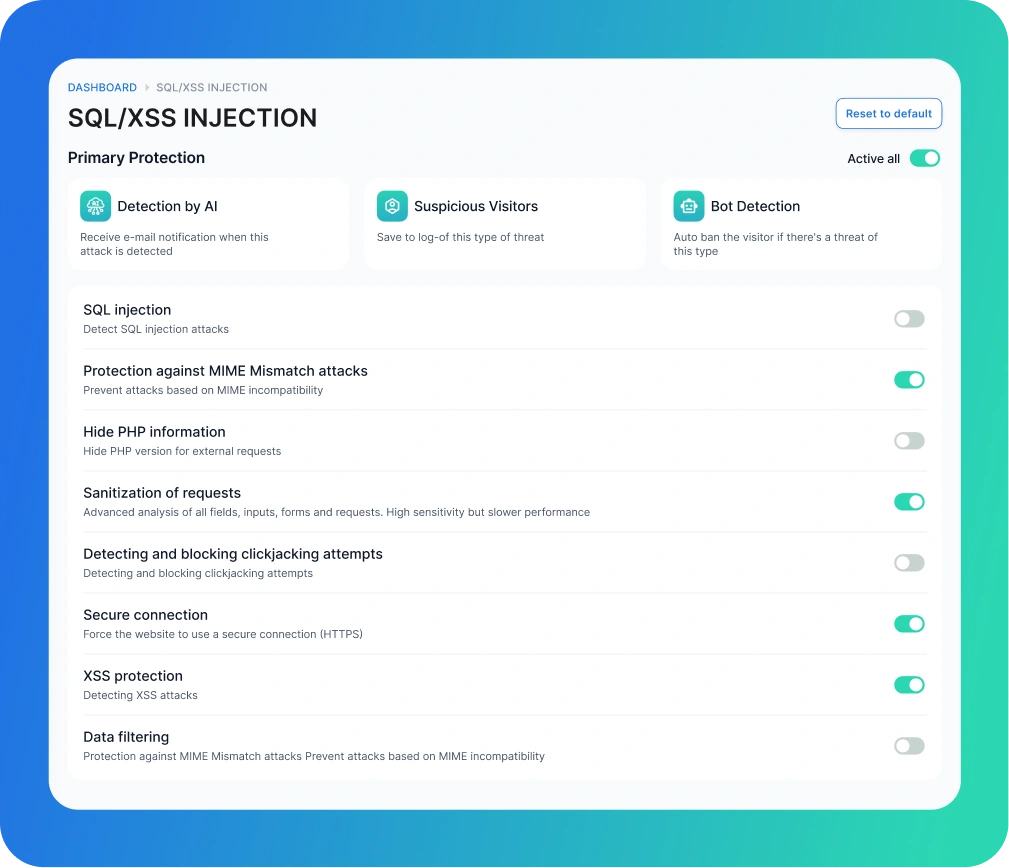
SQL/XSS Injection
-
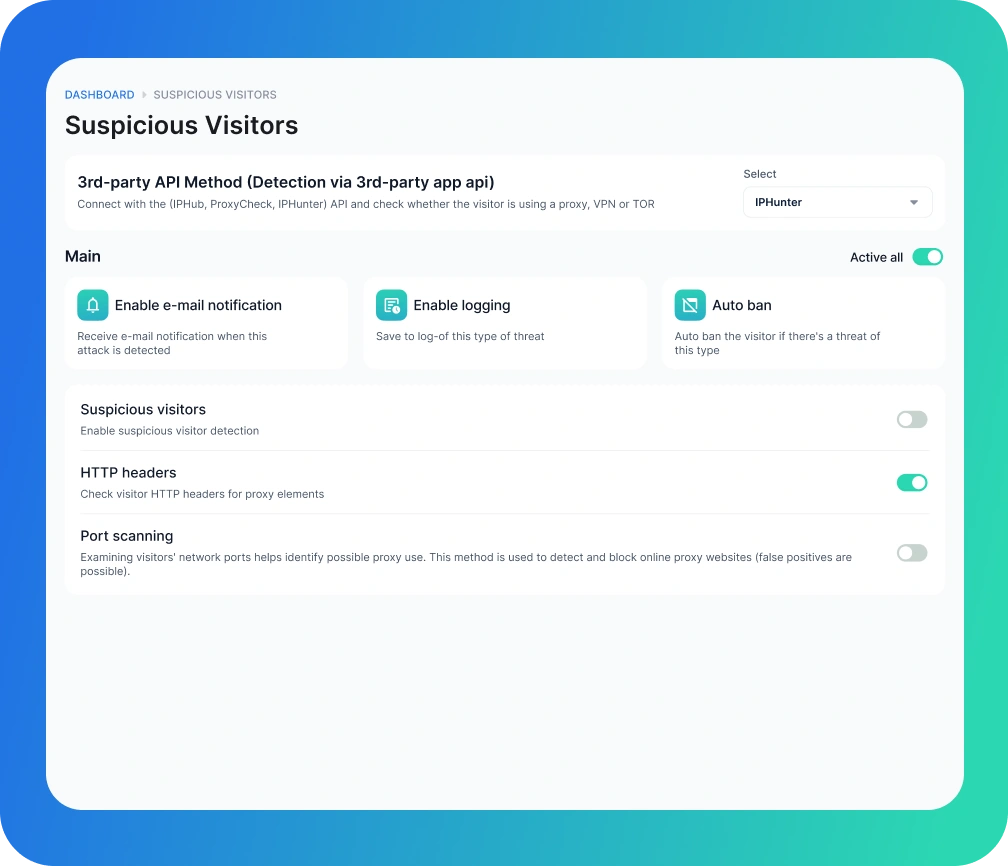
Suspicious Visitors
-
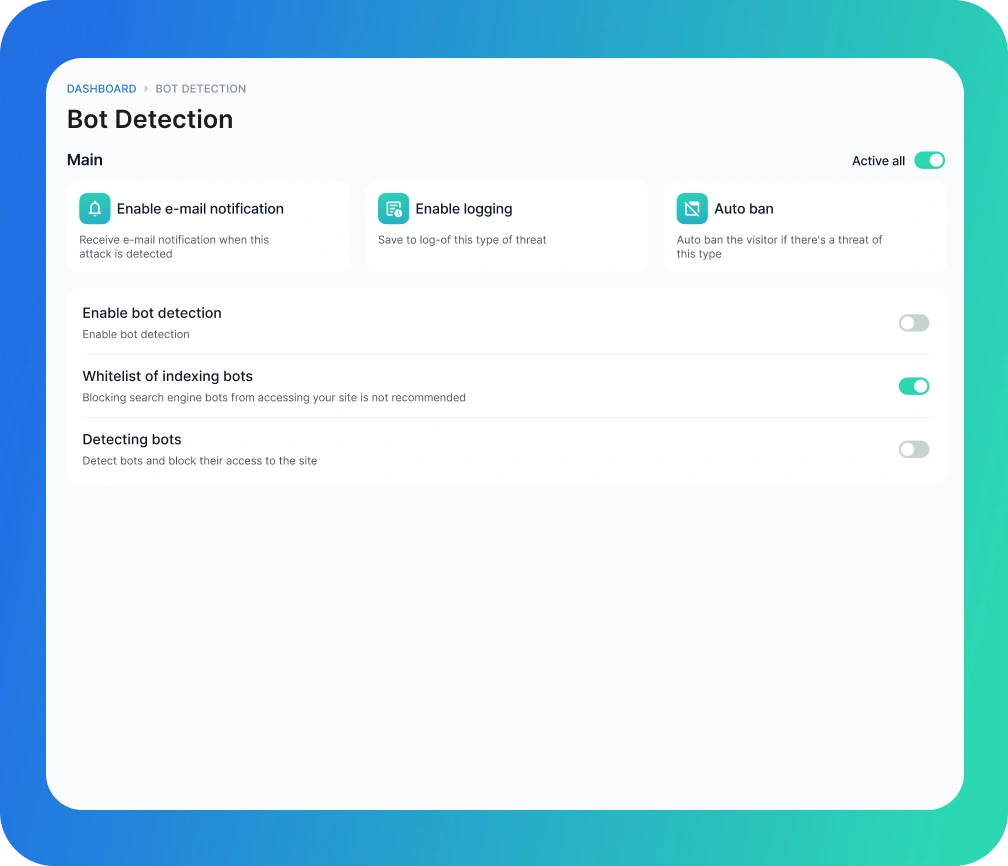
Bot Detection
-
IP Management
-
Threat Log
-
SQL Injection Protection
Our solution identifies and block attempts to exploit SQL injection vulnerabilities, safeguards your database from unauthorized access and modifications.
-
AI-Enhanced SQLi Detection
This Advanced Feature uses artificial intelligence to improve the detection Of SQL injection attacks. By analyzing patterns and anomalies that traditional methods might overlook, our AI-driven system provides a superior level of protection against SQLi threats.
-
XSS Protection
Our solution detects Cross-Site Scripting (XSS) attacks, which can inject malicious scripts into your web pages viewed by users.
-
MIME Mismatch Attacks
Our system safeguards your site from MIME mismatch vulnerabilities. preventing attacks that exploit inconsistencies in data types.
Our system includes a module that identifies and monitors suspicious visitors. it helps administrators take proactive measures to protect your web applications, ensuring robust security.
-
IP Reputation
This method assess whether a visitor uses a proxy, VPN, or Tor network.
-
HTTP headers
Check visitor HTTP headers for proxy elements
Enable Bot Detection
-
Detect and Block Malicious Bots
This feature identifies and blocks malicious bots that might attempt to scrape content, execute harmful actions, or overload the server with requests. By enabling bot detection, you protect your site from potential security risks and performance issues caused by these unwanted visitors.
Whitelist of Indexing Bots
-
Allow Legitimate Search Engine Bots
Blocking legitimate indexing bots from search engines like Google, Bing, Yahoo, Baidu, or Yandex can negatively impact your site’s visibility and ranking in search engine results. Therefore, a whitelist is implemented within the bot detection settings to ensure these bots can access your site for indexing purposes without being blocked.
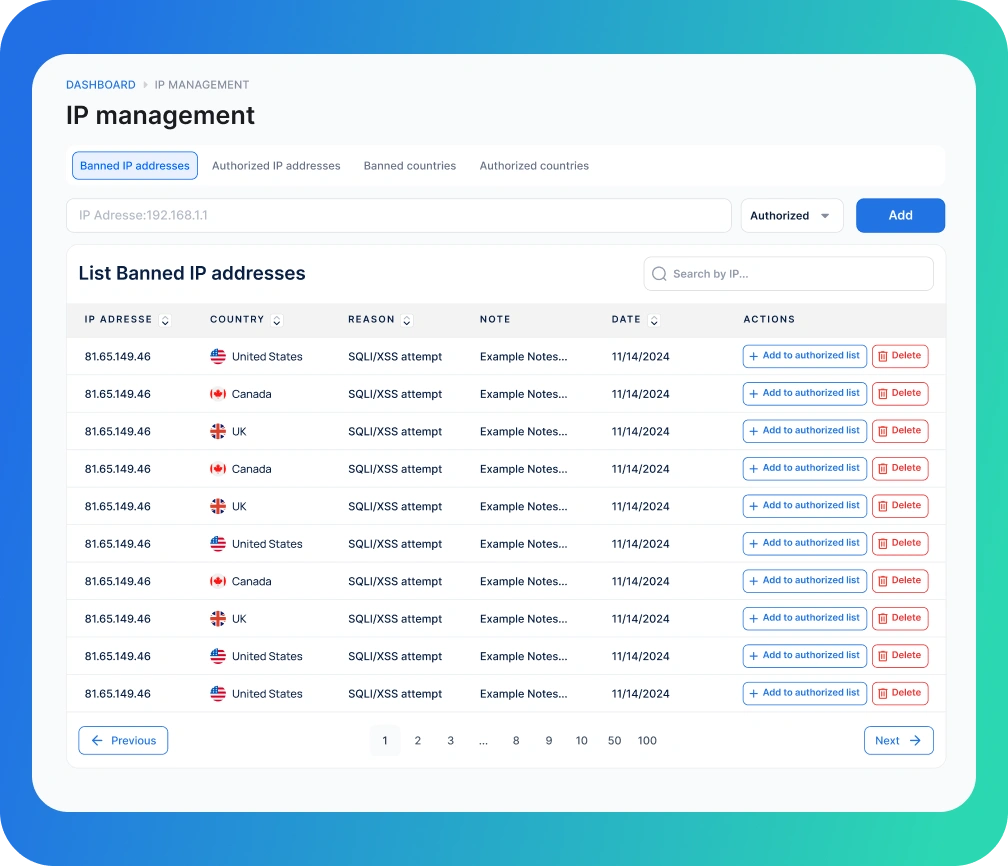
- This module allows you to manage IP addresses and Country accessing your website.
-
Automated Blocking
When the “Auto Ban” option is enabled, the system automatically detects and blocks IP addresses that engage in suspicious activities. These addresses are listed under the “List of Banned IP Addresses” section.
-
Manual Blocking
Manual Blocking: You can block an IP address by adding it to the list with the reason for the ban.
-
Blocking Countries
You can block traffic from specific countries to prevent access from regions considered high-risk or irrelevant to your operations.
-
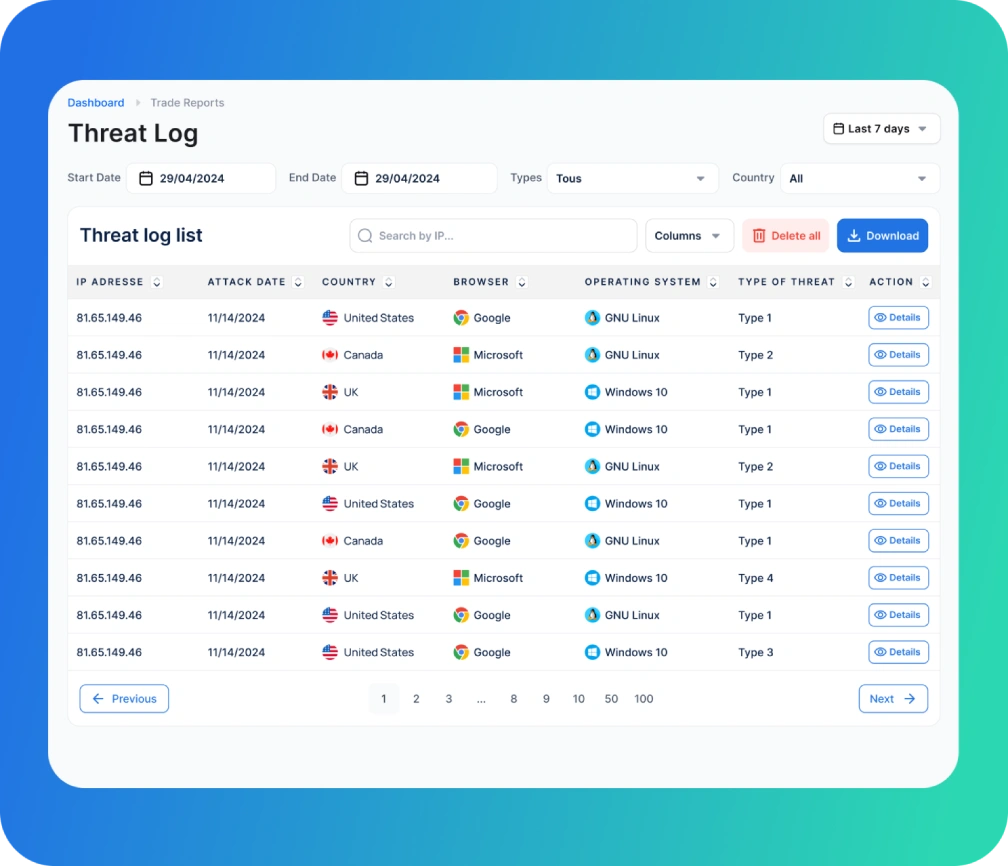
Detailed Attack Insights:
Each entry in the log provides comprehensive details about the attack, helping security analysts understand the context and specifics of each threat.
-
Search and Filter
Users can search for specific entries using the IP address or filter the data based on several criteria, including start and end dates, domain, type of attack, and country. This functionality allows for efficient monitoring and analysis of security threats.
-
Multi-Criteria Filtering:
The ability to filter by fields such as IP address, date, domain, type of attack, and country makes it easier for users to isolate specific incidents or patterns.
-
Customizable Date Range
Users can customize the viewable logs by selecting specific date ranges, focusing on periods of interest or during which unusual activity was noted.
What They Say About Us
Outstanding security service. The support team ensured seamless protection for our online library.

Bac Tunisie
E-Library
Securas Team has a team of high skilled professionals who are always up-to-date with the latest cyber security trends.

Hostiko Limited
Webhosting Company
Excellent service and support. Our online shop is now much more secure. Highly recommended!

Best Box TV
Electronic Shop
Contact Us
Have any questions or need assistance? Feel free to reach out to us using the form below. We’ll get back to you as soon as possible!